Yazam Processes
Conventional Security
Unconventional Threats
Traditional endpoint and browsing security applications (such as ● Firewalls ● Antivirus/Antimalware ● Web proxies ● Secure browsers ● EDR/XDR ● WAF ● Sandboxes) are essential for broad protection. Still, often fail to handle complex file structures and cannot proactively neutralize threats within files. They focus on detection and blocking after the file has landed, often failing against novel malware.
Risky Pathways
By Endpoint Applications
Endpoint applications serve as a primary conduit for files entering your protected network.
Many files are entered using web browsers:
● Google Chrome ● Microsoft Edge ● Mozilla Firefox.
Many files are entered using chat and messaging platforms, like: ● WhatsApp ● Telegram ● Signal ● Zoom ● Microsoft Teams ● Amazon Connect ● Google Meet ● and many more.
Incoming external files can contain and introduce significant security risks, while they often leverage the encrypted traffic to bypass scrutiny.
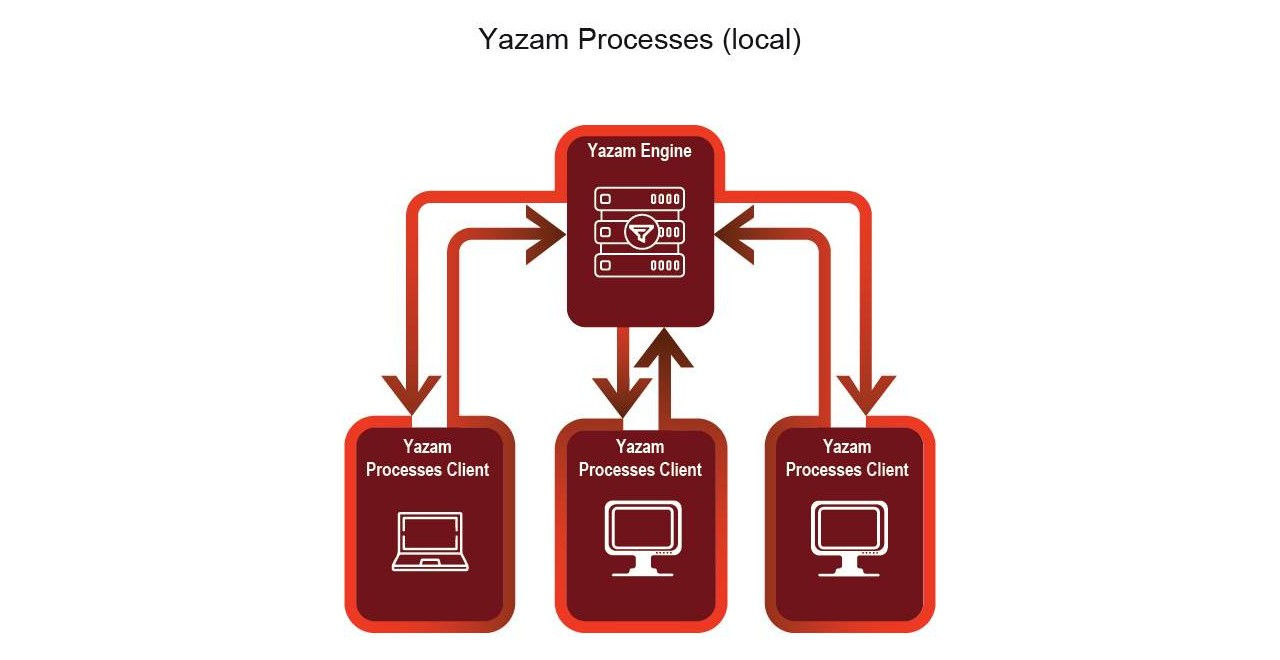
Yazam Processes
Provides an indispensable layer of protection for files entered via endpoint applications. It actively implements our unique CDR technology to remove embedded threats by intercepting, disarming, and reconstructing files, even when endpoint applications encrypt the traffic.
This ensures that every file entered by endpoint applications is clean, maintaining productivity without compromising Security.
Main features:
-
CDR filtering to files that are entered into the workstation using web browsers: ● Google Chrome ● Microsoft Edge ● Mozilla Firefox.
-
CDR filtering to files that are entered into the workstation using chat and messaging platforms, like ● WhatsApp ● Telegram ● Signal ● Zoom ● Microsoft Teams ● Amazon Connect ● Google Meet ● and many more.
-
CDR filtering to files that are entered into the workstation by additional local applications.
-
User sees the CDR filtering results in real-time.
-
Users' location can be both on-site and external (hybrid).
-
Yazam Processes client is installed on the workstations. No loading, no conflicts with other clients.
-
Yazam Engine can be installed on-premise or supplied as a service (SaaS).
-
User interface to supply passwords for encrypted files.
-
User management, Active Directory connecting.
-
Isolation between users.
-
Logging both for the filtering process and the CDR filtering results.
-
Quarantines blocked files and internal objects.
-
Multilingual user interfaces.
-
Speedy filtering process on standard hardware.